We specialize in providing a wide range of services and solutions to businesses and individuals.

Video Surveillance
We offer customized systems to meet the requirements of the diverse marketplace. From commercial to residential we have provided our customers with leading edge security solutions. Our goal is to enhance safety and improve operational efficiencies. Video Surveillance is necessary in preventing losses and protecting your assets. In addition to operating 24 hours a day/ 7 days a week, it is a valuable resource to deter any fraudulent activity plus the digital recording.
Alarm Systems
Alarm systems are the modern-day sentinels that stand guard over your peace of mind. They provide a robust shield against unexpected threats, instantly alerting you and the authorities to any potential dangers, be it intruders, fires, or emergencies. With cutting-edge technology and smart features, these systems offer convenience and real-time awareness, allowing you to control and monitor your security from anywhere.

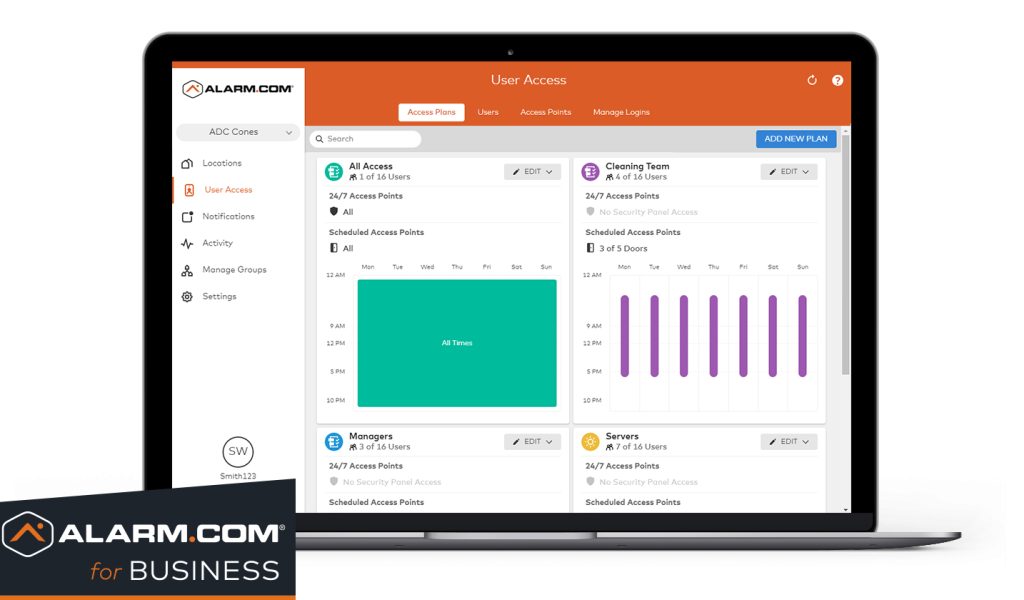
Alarm Monitoring
Alarm monitoring is your unwavering guardian, keeping a vigilant eye on your safety and security around the clock. With advanced technology and trained professionals at the helm, it serves as the ultimate insurance against threats to your home, business, or assets. From detecting burglaries and fires to medical emergencies, it’s the safety net that instantly notifies you and the appropriate authorities, delivering rapid response and peace of mind. In an unpredictable world, alarm monitoring is your ever-watchful protector, ensuring you’re prepared for whatever challenges may arise.
Access Control
Access control is the digital fortress safeguarding your most valuable assets. It empowers you to determine who enters, who stays, and who’s denied, ensuring your data, systems, and physical spaces are impervious to unauthorized intrusion. Whether you’re guarding sensitive information, securing critical infrastructure, or preserving privacy, access control is your sentinel, allowing you to grant, restrict, and monitor access with precision, bolstering your security and peace of mind.


Virtual Guarding
Virtual guarding is the cutting-edge security solution that combines human expertise with advanced technology to provide unparalleled protection for your property. Highly trained security professionals remotely monitor your premises using state-of-the-art cameras and sensors, instantly responding to any suspicious activity. This proactive approach not only deters potential threats but also allows for immediate intervention. Virtual guarding offers cost-effective and scalable security, ensuring your peace of mind, and allowing you to focus on what truly matters.
Security Laminate
Security laminates for windows and doors provide added protection against break-ins, vandalism, storms, and UV damage. They deter burglaries, smash-and-grab thefts, resist vandalism, and offer storm protection. Some laminates also reduce noise, enhance privacy, and provide ballistic and blast resistance for high-security environments. Overall, they bolster security, safety, and durability for homes and businesses.


Security Doors
Security doors are essential for your business as they act as a formidable barrier against unauthorized access, significantly reducing the risk of break-ins, theft, and vandalism. They not only enhance the overall safety of your employees but also protect valuable assets and inventory. Additionally, having security doors can help your business comply with regulatory requirements in certain industries, ensuring legal compliance.
Security Screens
Security screens serve as a strong deterrent against break-ins and unauthorized access, acting as a robust physical barrier. They provide added protection for storefronts, windows, and entry points, ensuring the safety of employees and the security of valuable assets. Moreover, security screens can enhance the overall appearance of a business while still allowing for visibility and natural light. With their durability and effectiveness, security screens are a smart investment in safeguarding both the physical and financial well-being of a business.


IT Services
IT services are the backbone of today’s businesses, providing the critical support and infrastructure needed to thrive in the digital age. Whether you’re a small startup or a large enterprise, IT services offer tailored solutions to streamline operations, enhance efficiency, and ensure data security. By outsourcing IT services, you gain access to expert knowledge and resources, saving time and money while staying competitive in an ever-evolving tech landscape.
Offsite Backups
Offsite backups refers to the practice of securely storing copies of important data and files at a location physically separate from the primary business or data center. This strategy serves as a crucial disaster recovery and data protection measure. Offsite backups are typically conducted using secure cloud storage or remote data centers, offering scalability and accessibility while safeguarding against local risks that could threaten data integrity and availability.


Data Recovery
Data recovery is the process of retrieving lost, damaged, or inaccessible digital information from storage media or systems. It’s a critical service in IT and data management, especially when data is accidentally deleted, becomes corrupted, or is rendered inaccessible due to hardware failures, software glitches, or cyberattacks. The goal of data recovery is to retrieve as much of the lost data as possible and restore it to a usable state, ensuring that businesses and individuals can regain access to vital information and minimize the impact of data-related setbacks.
Cyberecurity
Cybersecurity is the practice of safeguarding digital systems, networks, and sensitive information from a wide range of threats, including cyberattacks, data breaches, and unauthorized access. It encompasses a comprehensive set of strategies, technologies, and best practices designed to protect computers, servers, mobile devices, and the vast interconnected infrastructure of the digital world. Cybersecurity measures include the implementation of firewalls, antivirus software, encryption, multi-factor authentication, and regular security updates, among others.


Managed Services
Businesses and organizations opt for managed services to offload the day-to-day management, monitoring, and maintenance of their IT infrastructure, systems, and applications. These services typically encompass a wide range of IT tasks, including network management, data backup and recovery, cybersecurity, software updates, hardware maintenance, and technical support. Managed services allow organizations to focus on their core competencies while leaving the technical aspects of IT to experienced professionals.
VOIP
Voice over Internet Protocol (VoIP) is a technology that enables voice and multimedia communication over the internet rather than traditional analog phone lines. With VoIP, voice data is converted into digital packets and transmitted over IP networks, allowing for cost-effective and efficient communication. It enables users to make calls, send messages, and conduct video conferences using internet-connected devices like computers, smartphones, and IP phones. VoIP offers lower costs, flexibility, scalability, and a wide range of features like call forwarding, voicemail, and conference calling.

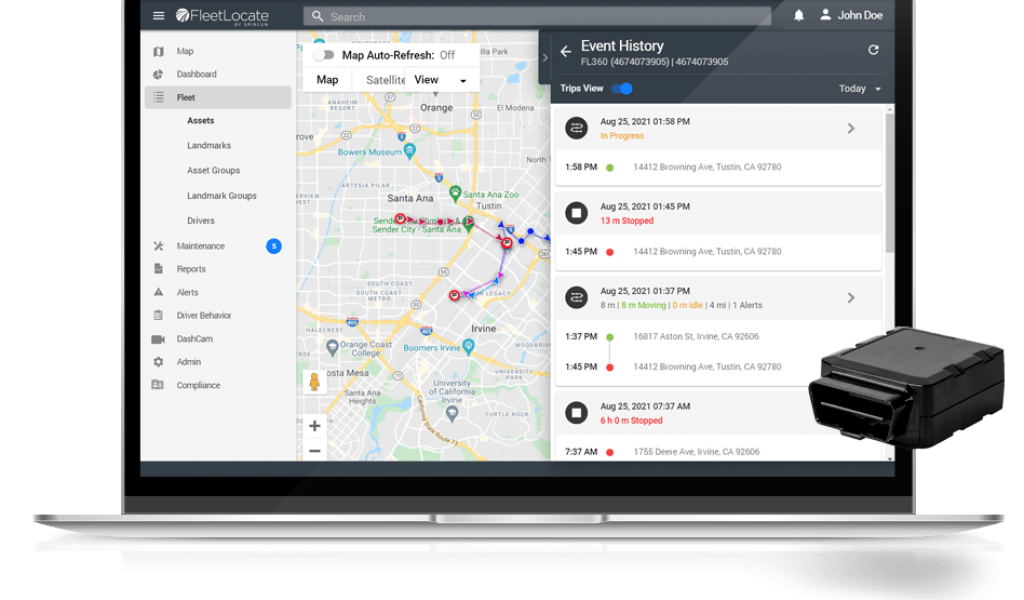
GPS Tracking
Get Visibility to Your Fleet and Drivers 24/7
Get the leading IoT solution for location information, analytics, and actionable insights on your assets and drivers in real time. Use comprehensive data to increase dispatch efficiencies, reduce vehicle misuse, improve customer service, and drive revenue. Our FL360 is a modular GPS tracking device that supports all vehicle types. It can be easily installed as a plug-and-play option, or as a covert installation.
Cellular Backup
Cellular backup is a crucial component of modern security and communication systems, providing a fail-safe mechanism in case of primary internet connectivity failures. It involves the use of cellular networks, such as 4G or 5G, as a secondary data connection when the primary internet connection, like broadband or Ethernet, becomes unavailable. In the event of an internet outage or physical line disruption, cellular backup automatically kicks in, maintaining connectivity and allowing critical data transmission and communication to continue seamlessly.

Structured Wiring
Structured wiring is the invisible force that weaves a tapestry of connectivity throughout your home or business, creating a network that seamlessly powers your digital life. With this meticulously designed infrastructure, you gain access to lightning-fast internet, crystal-clear communication, and integrated smart systems, all from a single, organized source. It future-proofs your property, accommodating new technologies with ease, while increasing its overall value.
